Complete protection for workstations, servers, and mobile devices
State-of-the-art technologies to defend against ransomware, exploits, and the like.
Central and easy administration of clients
The ECSO quality label: "Cybersecurity Made in Europe
G DATA is one of the first security companies to be awarded the "Cybersecurity Made in Europe" label by the European Cyber Security Organisation (ECSO). This means that we fully meet the following criteria:
- the company's headquarters are located in Europe
- the majority of the employees are employed in Europe
- the main market is Europe
- compliance with the 12 basic security requirements, which ENISA has defined as indispensable for secure products and services in the field of information and communication technologies: download.


Integrated solutions to protect your end devices
The most sensitive areas of your systems are your employees’ workstations. Where attachments are opened, passwords are entered, and sensitive data is processed. The servers that make connections across the entire network. And smartphones that come and go with your employees every day. This is precisely where our endpoint security solutions protect your company assets.
Defense against cyberattacks
Malware protection
Secure e-mail communication
Policy Management
Gateway Security
The technologies behind our Endpoint Security

Track down criminal hackers faster
Our proprietary DeepRay® technology effectively defends your business against the threat of camouflaged malware using artificial intelligence and machine learning.

Malicious processes. Stopped with pinpoint accuracy.
BEAST provides unmatched protection against previously unknown malware. Our software captures all system behavior and blocks malicious processes before they can cause damage. With full maintenance of your system performance.
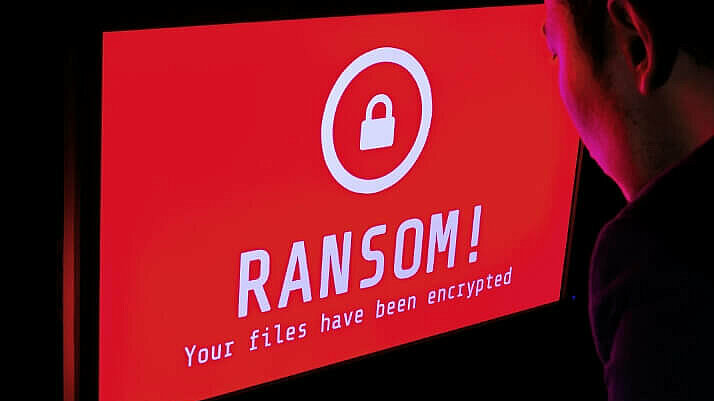
Reliable protection against blackmail Trojans
If ransomware infects a company network, it can cause damage reaching into the millions within a very short time. Our special anti-ransomware module protects you from criminals encrypting your data and taking it hostage.

Innovative. Fast. Uncompromising.
Two perfectly complementary engines ensure that your systems enjoy maximum protection at all times. Your employees don’t even notice – they can concentrate on their work without being disturbed.

Undiscovered vulnerability? Not a problem.
Software errors that have not yet been corrected pose a high risk to the security of your data. Our G DATA Exploit Protection means you are protected against this: it prevents criminals from exploiting both known and previously undiscovered vulnerabilities.
Which solution is right for your company?
Antivirus Business
Security for all endpoints
Next-generation protection technologies
Central management
Mobile Device Management
Optional modules
Client Security Business
Security for all endpoints
Next-generation protection technologies
Central management
Mobile Device Management
Anti-Spam
Firewall
Optional modules
Endpoint Protection Business
Security for all endpoints
Next-generation protection technologies
Central management
Mobile Device Management
Anti-Spam
Firewall
Policy Manager
Optional modules

Save resources – outsource IT security
Managed Endpoint Security
Outsource your IT security and benefit from the full functionality of our endpoint security solutions. Your G DATA partner will take over all respective tasks for you – from rolling out the antivirus software to configuring the firewall. On-premise or in the cloud as required.

24/7 Support
The service and support team are located in Bochum – right next to the software development team. You can reach our experts at any time by phone or by e-mail, 24 hours a day, 365 days a year.