What do you have on your computer? Important emails, secret files from the office or even old photos of your children? During the course of a computer's life, a lot of data which may be personal, perhaps even business related but in any case sensitive, accumulates on the hard disk. And that is what makes you vulnerable to blackmail. If instead of your usual start screen suddenly only a skull or a blackmail letter appears on your monitor, you probably are dealing with ransomware.
What does "ransomware" mean?
“Ransomware” does exactly what is says: it holds data or systems for ransom. Experts sometimes talk of encryption Trojans as well: the ransom scheme is based on the fact that this type of ransomware encrypts the user's data. The other names indicate how ransomware functions. It steals its way into the system, often disguised as a legitimate program – and the user realises with horror that the computer has been locked.
How does ransomware make itself known?
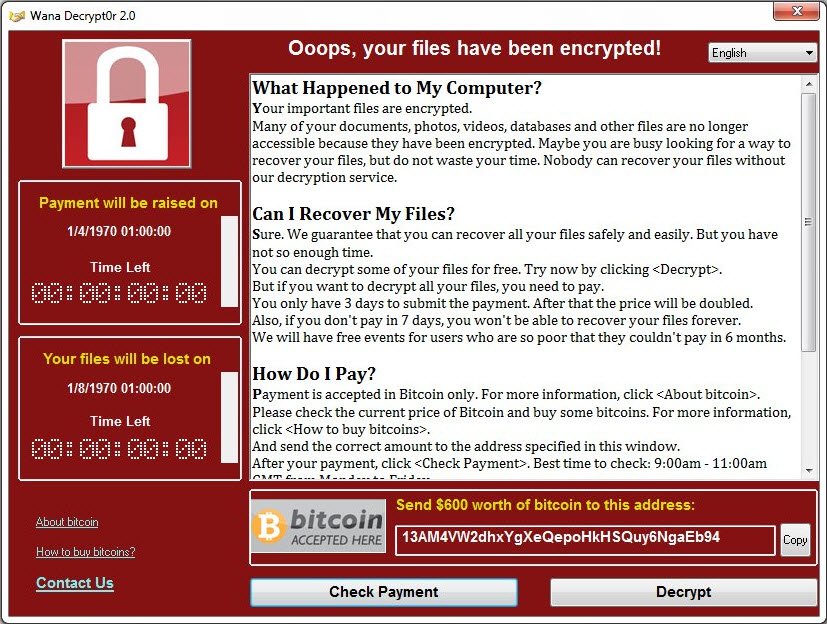
Generally, a locked screen or ransom note that cannot be removed is the first thing that the user sees of the ransomware. Some ransomware variants have an incubation period, meaning that the malicious effects are only seen when the user can no longer remember when and where he might have picked up a ransom Trojan.
Ideally, malware can be detected by a virus scanner and appear as a positive scan result. However, people with no antivirus solution installed will only notice ransomware when it is already too late. As many ransom Trojans delete themselves again after running their malicious function, it is a real challenge for security software to detect the malware. The first thing that the computer user sees of the ransomware is an information window with a payment demand that cannot be removed.
Ransomware examples
How important is the subject of data protection to users?
... of all users worldwide have never backed up their system.
Source: World Backup Day
... of all survey participants are afraid of loosing photos and videos.
Source: Survey Acronis
... of all users use external hard drives for their data storage.
Source: Survey Kroll Ontrack
How could I possibly have picked up ransomware?
The tricky thing about ransomware is that, like the majority of Trojans, it hides itself behind apparently harmless links or file formats. The encryption Trojan Petya, for example, distributes itself when unsuspecting users open a Dropbox file. The user downloads the malware in doing so. If he then clicks on the file downloaded to his PC, he executes the file – and Petya starts to distribute itself across the system. Petya is therefore reliant upon the involuntary assistance of the user, who believes he is opening a standard file but is actually triggering the installation of the ransomware.
This means that its distribution paths are hardly any different from those of other types of malware. The files often get onto the computer via a manipulated website, reached via a link in a spam email or a message on a social network. Sometimes the perpetrators send out their own emails that contain a supposed reminder or a delivery note. However, in reality, there is malware rather than important information hiding in the attached file.
How long has ransomware been around?
Blackmailing PC users in this way is nothing new. The first documented ransomware, the AIDS Trojan disk, was circulated back in 1989 – and distributed via a diskette at the time. The evolutionary biologist and Harvard graduate Joseph L. Popp sent out 20,000 infected diskettes with the header "AIDS Information - Introductory Diskette" to the participants of the World Health Organization's International AIDS Conference and so smuggled the ransomware onto their computers. The malware replaced a system configuration file (autoexec.bat) and, after ninety restarts, started to encrypt the hard drive. In order to access the data again, the victims had to send US$ 189 to a company called PC Cyborg in Panama – which is why the first ransomware was also known as the PC Cyborg Trojan.
What happens exactly when ransomware gets onto the computer?
Clicking on a link in an email to a website or Dropbox triggers an installer download – this is how the encryption Trojan Petya successfully infected so many computers in spring 2016. Petya forces the computer to restart and then replaces the master boot record (MBR) with a malicious loading routine. Petya then forces the computer to restart again and pretends to the user that the file system structure is being checked, as is the case for example after a system crash. But Petya is not in fact checking the system for its functional efficiency. Petya does not encrypt the data itself – it just makes it inaccessible to the user. The computer can no longer detect the files and cannot even determine whether they are still there. After yet another enforced restart, the lock screen appears with the blackmailers' demands. With many types of ransomware, it is difficult by this stage to decrypt the files without making a payment. Petya, however, has now been decrypted, so nobody needs to make a ransom payment any more to get their data decrypted again.
How does ransomware work?
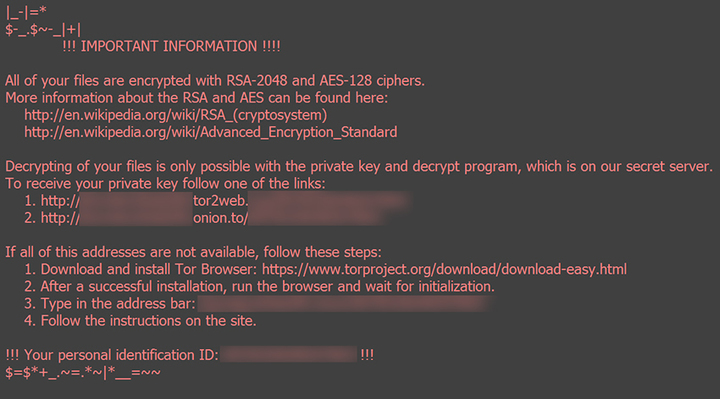
Initially, ransom programs mainly used to block the desktops of individual PCs. Nowadays these rather small attacks have become quite rare. Encryption programs are found much more often than such screen lockers these days. With these, the contents of the hard drive are encrypted in such a way that the user can no longer access them. Generally, a website or form mask is displayed on the lock screen that explains the demands and the payment methods. The blackmailers promise that they will decrypt the data again after the payment has been received.
More hardened perpetrators threaten to have the data permanently deleted if the victim contacts the police. There is now even ransomware that deletes encrypted files for every hour for which the payment is not made. And to prevent the user from riding out the threat by switching off the PC, the software deletes a thousand files when the system is restarted.
And how has the threat situation changed since then?
The first encryption Trojan distributed via the net was TROJ_PGPCODER.A. The blackmailers demanded several hundred dollars to decrypt it. That was in 2005. Since 2011, security experts have recorded a rapid increase in ransomware attacks. The German Federal Office for Information Security (BSI) warned: "Since mid-September 2015, the threat situation from ransomware has significantly intensified." In Germany especially, virus scanners have increasingly been coming across ransomware since early 2016, added the BSI. Security solutions found more than 10 times as much ransomware in Germany in February 2016 compared to October 2015. This trend is also seen across the rest of the world – globally the number of detections has increased by a factor of 6 during this period.
How exactly do the blackmailers earn money from this?
The increase in the number of ransomware files being circulated is down to the fact that they are now so easy to produce. There are so-called crimeware kits on the Darknet that can be used to put together malware on a modular principle. It is also very easy and cheap to program ransomware – or have it programmed. The criminals put in a little money to generate it, but they can earn a great deal back in the best cases. The perpetrators inform the victims of the payment options via the lock screen. The cyber criminals get paid via Paysafe or Ukash cards or with the Bitcoin online currency. The ransom is in the region of 400 Euros in many cases. However, sometimes several thousand Euros are demanded for the decryption. It depends on how important the data is, such as with the blackmailing of hospitals with Locky. When the victim has made the payment, it is credited to the perpetrator – and ideally the data is released again in return.
How can I protect myself?
- Backups: The best protection against ransomware is to perform regular backups. Those must be stored on a medium separate from the system. If you run a backup to an external hard disk, remove it after the backup and ensure that this storage medium is offline unless it is needed. With regular backups you can ensure that you do not lose any data in the event of an actual ransomware infection and can easily restore your system. When doing so, make sure to use a secure medium such as a CD that cannot also become infected.
- Operating system: In addition to this, regular updates your operating system should be performed. In this way you can close security holes. The same applies to your browser and any other software installed on your system.
- Browser protection: Browser protection is also useful for protecting you from dangerous scripts and from accidentally downloading malware.
- Email protection: Bogus and fraudulent emails can be made secure while still in your inbox via special security software. That way, such emails are no longer a problem. Antivirus software also detects malware such as Trojans and deletes it.
- Ransomware-Cleaner: There is a software solution against screen lockers, which helps you to remove the lock screen and the threat alike.
- User account: An infection can also be prevented if the user does not log in with his admin account at all times, but sets up a guest account instead. As this account has fewer rights, ransomware cannot penetrate as deeply into the system and, ideally, will not cause any damage.
Will the perpetrators really decrypt my data if I pay the ransom?
Caution and scepticism is always advised when dealing with criminals. Many of the criminals have no interest in fair play from the outset – and some have not even made plans for a decryption option. For them it is all about the money. Anyone who has not made a backup copy will inevitably lose their files after the computer has been infected with ransomware. Hence there is something to be learned from action films – do not negotiate with blackmailers.
The German Federal Office for Information Security (BSI) advises against following up on the demands. Nobody should hope to be treated fairly by criminals. Also, anyone paying a ransom via credit card is turning their account into a self-service shop. A blackmailer also can suddenly demand more money to release the data, or encrypt the data once again at a later date via a backdoor in the system and demand more money – even if appears at first that he has kept his promise and released the data. Therefore, paying a ransom is a risk on multiple levels.
What do I need to look out for if I want to pay the ransom?
If you want to pay the ransom despite all the warnings, you should not remove any of the components of the ransomware from the PC beforehand. Depending on the circumstances, these might be the lock into which you need to put the key you might receive after making the payment. Without a lock, the decryption code might be unusable – and your data will remain irretrievably encrypted. Furthermore, the components may be important in the event that the investigative authorities succeed in striking back at the cyber criminals – there are often decrypters that can help those affected recover their data without making a payment. The information contained in the components would then be required for generating the recovery key.
If you have actually received a key and have been able to decrypt your files with it, you should then immediately delete the ransomware from your computer. However, you should never lose sight of the fact that the criminals do not feel obliged to you in any way and that you may have lost money and data. Also keep up with the criminals' machinations. Because if nobody pays them, the distribution of ransomware will not be worthwhile for criminals anymore.
How do I remove ransomware?
If you have become the victim of an attack despite your best efforts, only one thing will help: removing the malware from your computer. The most reliable and thorough way of removing ransomware is to reset the system to the factory settings. Before you choose this option, you should realise that all of the files on the computer will be irretrievably lost afterwards. Alternatively, if you have carried out regular system backups, you can reset your system to a point in time before the infection occurred. Select the most recent restore point. When doing so, you must always ensure that this point is indeed before the time of the infection. In this way you can rid your computer of the malware.
Ransomware in detail
– Expertise on the subject –
Encryption Trojans
An encryption Trojan or crypto-Trojan encrypts files on the computer and requires ransom for decryption. Some Trojan families encrypt only certain file types, such as images, documents, or movies. Others encrypt all file types and spare only a few folders. Popular families are CryptoLocker (no longer active), CryptoWall, CTB-Locker, Locky, TeslaCrypt and TorrentLocker. A fairly new form is Petya. Instead of encrypting individual files, it encrypts the Master File Table (the table of contents) of the hard disk. After which the files can no longer be found on the hard disk.
App-Locker
This type of ransomware blackmails users by preventing access to apps and programs. For example, the browser or access to the management of the network storage (NAS) is blocked. In some cases they can be overridden with standard tools. There are only a few malware families of this kind, one example is Synolocker. The name is derived from the fact that the malware company is targeting products from Synology - a manufacturer of NAS solutions.
Screenlocker
A screenlocker blocks access to the computer by displaying a lock screen that constantly moves to the foreground and may also terminate other processes. As a result, the computer can no longer be operated. The best-known family in this category is Reveton, also known as BKA-Trojans, GEZ-Trojans or FBI-Trojans.
Hybrids
There is also ransomware that combines screenlocker and encryption. This makes restoring the data even more time-consuming. Also here there are only a few categories, e.g. Chimera.

![[Translate to English UK:] The ways of infection [Translate to English UK:] We show you how your computer could be infected.](/fileadmin/_processed_/2/5/GDATA-Infographic-Ransomware-Petya-Infektionsweg-1040_RGB-EN_8534da8d85.gif)
