They permeate the Internet like a gigantic spider’s web. Botnets link computers to huge networks – without the majority of us knowing anything about it. Criminals manipulate computers, connect them and use them for their own purposes. The result is a network of infected PCs, remotely controlled by “botmasters”. Botnets are among the largest sources of illegal money for cyber criminals. According to estimates, hundreds of millions of computers worldwide are affected. One of the biggest networks discovered comprised over 30 million computers. There is a fair chance that your own PC was part of a botnet at one point in time, too.
How does a botnet work?
The operators of a botnet smuggle malware called a bot (short for “robot”) onto other people’s computers. These bots operate in the background without the owner of the PC noticing anything maintain a low profile. The computer is then exploited for the purposes of the botmasters, none of which the user would voluntarily agree to. As the computers are being controlled remotely and so are acting “involuntarily”, parts of the botnet are also known as “zombie PCs”.
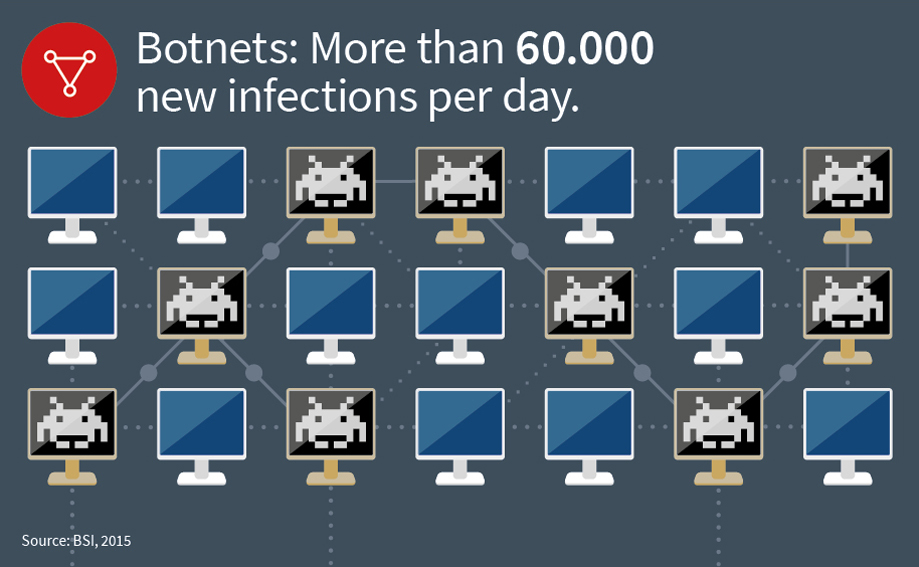
The bots operate via the Internet. This means that they only work when the computer is switched on and is connected to the Internet. The more bots there are in a network, the greater the number of active computers at any one time. The German Federal Office for Information Security (BSI) recorded up to 60,000 new infections per day in the first quarter of 2015.* In purely technical terms, a botnet is a distributed computing network – a collection of computers working independently of one another. They do indeed communicate with each other occasionally, but they carry out their tasks independent from one another.
How do I detect a botnet?
If so many computers form part of a botnet, how can I tell if I am part of one?
- In some cases, the fact that the Internet connection has become slower or continually threatens to collapse under the strain can give away the presence of a botnet client. If the user has not significantly changed his data usage, this should be treated as a warning signal. However, other malware may also be responsible for a slow connection.
- One clear indication is if the virus scanner sounds the alarm.
- A look at the Task Manager can also offer some clues: Can you see new, peculiar or unfamiliar processes there which never have been present before? The same applies to autostart entries.
- As botnets are hard for lay people to detect, the emphasis should be on prevention instead of instinct.
What are botnets used for?
Botnets are used for all sorts of different things – and not all of them are illegal. The University of Berkeley in America provides the code for a good kind of botnet client. The voluntary connection of as many private computers as possible is designed to reduce IT costs for various research projects. For example, researchers use such a botnet to look for intelligent life in space.
However, the overwhelming majority of botnets are created against the will of the PC owners and are generally used for criminal purposes. Zombie PCs are used for things such as distributing spam. For example, phishing emails are sent out to the digital world by PC owners without them realising. Other botnets serve criminal organization as storage space or help provide the perpetrators obtain sensitive user data. Either this data is used by the perpetrators themselves or the information is monetized on the Darknet. Furthermore, a botnet enables the perpetrators to establish a connection to a third-party computer via the zombie PC and thus hide its original address. Another type of use for a zombie PC is as an intermediate host that infects other computers and so triggers a chain reaction."
How is a botnet created?
The majority begin with an infected website. Users with no active web protection who end up on such a site usually have malware foisted upon them without noticing. However, an attack can also take place via an email in which, for example, the bot’s installation program is hidden in an attachment, or there is a link to a manipulated website. Sometimes users also unintentionally install Trojans along with harmless programs, which open the door, as it were, to the installation of the bot.
In this way, PCs are turned into remote-controlled bots, where a cyber criminal is pulling the strings. These strings are networked in such a way that we should actually think of a botnet as a highly ramified spider’s web. This is how ordinary PCs become part of a botnet. According to the Anti-Botnet Advisory Centre operated by Internet association Eco, one in three PCs in Germany is thought to have been infected and be part of a botnet.
How can I protect myself against botnets?
- A good way to protect yourself against malware and the installation of bots is reliable virus protection and a properly configured firewall.
- Keep your browser up to date. According to the Anti-Botnet Advisory Centre operated by Internet association Eco, 80 percent of browsers on PCs in Germany are out of date. An update closes security holes that otherwise can be exploited by criminals. G DATA security solutions offer an additional layer of protection against the exploitation of security holes, even when there is no patch available for closing the hole – G DATA Exploit Protection.
- Set up your security software and programs in such a way that they update automatically. This will close security holes as quickly as possible.
- Install browser protection as well – this will protect you against unintentionally downloading malware without noticing, and against phishing sites.
- Many security solutions include email protection. This prevents you from being taken in by manipulated websites and potentially downloading a bot without realising.
- Do not click on attachments that make you sceptical. This especially applies to invoices that you cannot place. Have you actually ordered anything from the sender?
- You should also be suspicious of emails containing dubious spelling or messages that contain a link to your bank or a shopping platform. Your bank will never ask you to click directly on a link.
- During everyday use of your computer, use an account that does not have administrator rights, and only work with the administrator account in exceptional circumstances. This will reduce the risk of malware penetrating into deeper layers of your system and being able to carry out changes and execute files without restriction.
More information and sources
* The State of IT Security in Germany 2018, Federal Office for Information Security (BSI) (PDF 5,06MB)
![[Translate to English UK:] Botnets encompass computers from all over the world. [Translate to English UK:] Botnets encompass computers from all over the world.](/fileadmin/_processed_/b/6/G_DATA_Botnetstorm_71794e9c0f.jpg)